#TradeSecretsStolen- Chinese Hackers Caught Stealing Trade Secrets and Intellectual Properties from Multinational Companies
An elusive and sophisticated cyberespionage campaign orchestrated by the Chinabacked Winnti group has managed to fly under the radar since at least 2019.
Dubbed "Operation CuckooBees" by Israeli cybersecurity company Cybereason, the massive intellectual property theft operation enabled the threat actor to exfiltrate hundreds of gigabytes of information.
Targets included technology and manufacturing companies primarily located in East Asia, Western Europe, and North America.
"The attackers targeted intellectual property developed by the victims, including sensitive documents, blueprints, diagrams, formulas, and manufacturingrelated proprietary data," the researchers said.
"In addition, the attackers collected information that could be used for future cyberattacks, such as details about the target company`s business units, network architecture, user accounts and credentials, employee emails, and customer data."
Winnti, also tracked by other cybersecurity vendors under the names APT41, Axiom, Barium, and Bronze Atlas, is known to be active since at least 2007.
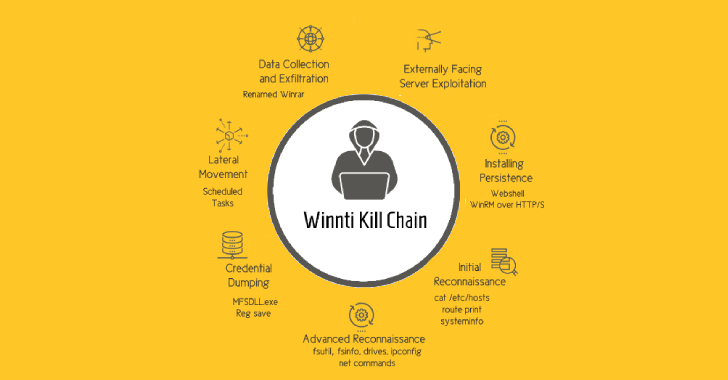
"The purpose of this group is to steal intellectual property from organizations in developed countries, which will be done on behalf of China and support decision-making in many Chinese economic sectors," Secureworks said. .. The multi-stage chain of infection documented by
Cybereason involves leveraging an internet-connected server to provide a web shell for reconnaissance, traversal, and data extraction activities. It will be.
Complex and complex, each component of the kill chain relies on other modules to function, making it very difficult to analyze following the "card house" approach.
"This shows the attention and effort devoted to both malware and operational security considerations, and analysis is almost impossible unless all pieces of the puzzle are put together in the correct order." The researchers explained.
data acquisition is facilitated by a modular loader called Spyder, which is used to decrypt and load additional payloads. It also uses four different payloads (STASHLOG, SPARKLOG, PRIVATELOG, and DEPLOYLOG). These payloads are sequentially deployed to destroy the kernel-level rootkit WINNKIT. The key to camouflaging the
campaign is to use "rarely seen" techniques, such as the abuse of Windows Common Log File System & # 40; CLFS & # 41 ;. A mechanism that hides the payload and allows hacking groups to hide the payload and avoid detection by traditional security products.
Interestingly, some of the attack sequences were already detailed by Mandiant in September 2021 and CLFS was being abused to hide the second stage payload to evade detection. I am paying attention.
Cyber-security companies have attributed the malware to an unknown attacker, but warned that it could have been deployed as part of a targeted activity.
“There is no tool that can analyze CLFS log files because the file format is not widely used or documented,” Mandiant said at the time. "This allows an attacker to easily hide the data as a log record because it can be accessed via API functions." As part of that, the
WINNKIT compilation timestamp is May 2019 on VirusTotal. The detection rate of is almost zero, reflecting its elusive nature. Of the malware that allowed the author to remain undetected for years. According to
researchers, the ultimate goal of the intrusion is to soak up proprietary information, research documents, source code, and blueprints for various technologies.
"Winnti is one of the most hard-working groups working for the national interest of China," said Cybereason. "The threat [actor] employed an elaborate, multistage infection chain that was critical to enabling the group to remain undetected for so long."



Comments
Post a Comment